Protection Job Options Explained
Overview
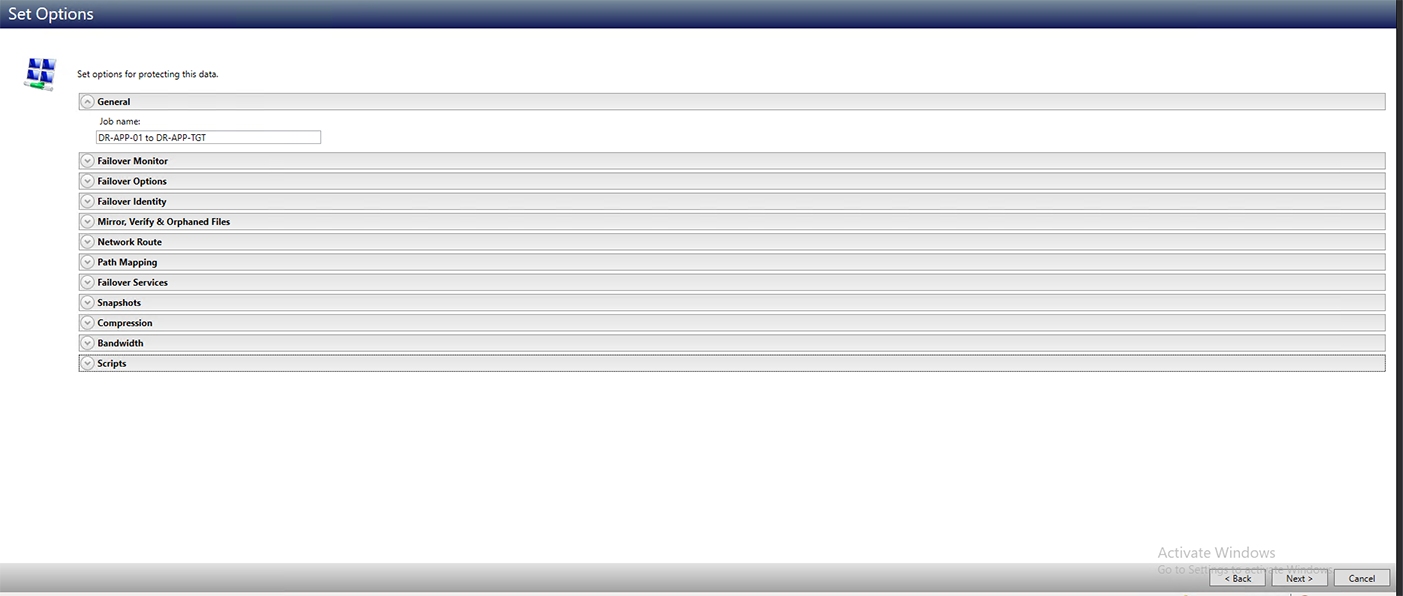
When accessing the wizard for creating a new Protection Plan (discussed in the next section, Protection Plan Configuration), after choosing the type of job and the target server for your job, you will be presented with the Job Options page:
Protection Jobs have a number of configuration options available during creation of a Protection Plan, which can be tweaked and modified based on the particular needs for the job and the environment. Reviewing this page thoroughly will help determine what options are best suited for your particular scenarios.
Note that there are different options available for File and Folder Protection jobs and Full Server Protection jobs. See the appropriate section below for the job type you are creating.
File and Folder Protection Jobs
General
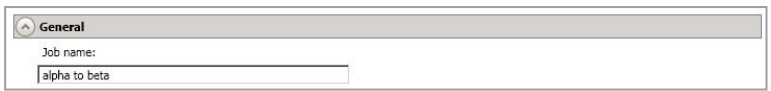
This field allows you to set the name of the job. Job names should be simple but descriptive enough for easy reference and review of function.
Failover Monitor
This section allows you to configure monitoring by the target of the source and, based on a predetermined set of options, enact an automatic cutover if necessary.
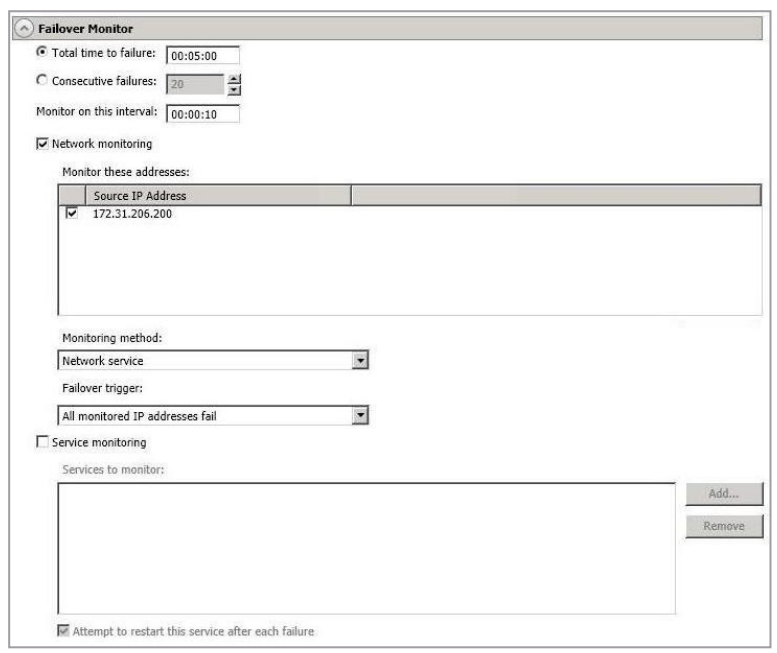
Option Details
- Total Time To Failure - Specify, in hours:minutes:seconds, how long the target will keep trying to contact the source before the source is considered failed. This time is precise. If the total time has expired without a successful response from the source, this will be considered a failure.
- Consider a shorter amount of time for servers, such as a web server or order processing database, which must remain available and responsive at all times. Shorter times should be used where redundant interfaces and high-speed, reliable network links are available to prevent the false detection of failure. If the hardware does not support reliable communications, shorter times can lead to premature failover. Consider a longer amount of time for machines on slower networks or on a server that is not transaction critical. For example, failover would not be necessary in the case of a server restart.
- Consecutive Failures - Specify how many attempts the target will make to contact the source before the source is considered failed. For example, if you have this option set to 20, and your source fails to respond to the target 20 times in a row, this will be considered a failure.
- Monitor On This Interval - Specify, in hours:minutes:seconds, how long to wait between attempts to contact the source to confirm it is online. This means that after a response (success or failure) is received from the source, SyncSafe Replicate will wait the specified interval time before contacting the source again. If you set the interval to 00:00:00, then a new check will be initiated immediately after the response is received.
- If you choose Total Time To Failure, do not specify a longer interval than failure time or your server will be considered failed during the interval period.
- If you choose Consecutive Failures, your failure time is calculated by the length of time it takes your source to respond plus the interval time between each response, times the number of consecutive failures that can be allowed. That would be (response time + interval) * failure number. Keep in mind that timeouts from a failed check are included in the response time, so your failure time will not be precise.
- Network Monitoring - With this option, the target will monitor the source using a network ping.
- Monitor These Addresses - Select each Source IP Address that you want the target to monitor. If you are using a NAT environment, do not select a private IP address on the source because the target cannot reach the source's private address, thus causing an immediate failure. Also for NAT environments, you will see an additional field for the Replication Service port. This gives you the ability to specify the port number to be used with the address, allowing the target to monitor the source through a router.
- Monitoring Method - This option determines the type of failover monitoring used. The Network Service option tests source availability using an ICMP ping to confirm that the route is active. The Management Service option opens a socket connection to confirm that the Double-Take service is active. If you are using a NAT environment, Management Service is the only available option.
- Network Service - Source availability will be tested by an ICMP ping to confirm the route is active.
- Management Service - Source availability will be tested by a UDP ping to confirm the Double-Take service is active.
- Network and Management Services - Source availability will be tested by both an ICMP ping to confirm the route is active and a UDP ping to confirm the Double-Take service is active. If either monitoring method fails, failover will be triggered.
- Failover Trigger - If you are monitoring multiple IP addresses, specify when you want a failover condition to be triggered.
- One Monitored IP Address Fails - A failover condition will be triggered when any one of the monitored IP addresses fails. If each IP address is on a different subnet, you may want to trigger failover after one fails.
- All Monitored IP Addresses Fail - A failover condition will be triggered when all monitored IP addresses fail. If there are multiple, redundant paths to a server, losing one probably means an isolated network problem and you should wait for all IP addresses to fail.
- Service monitoring—With this option, the target will monitor specific services on the source by confirming that they are running. Multiple services in the list will be checked in parallel. A failover condition is met when one of the monitored services fails the check. Click Add and select the service that you want to monitor. Repeat this step for additional services that you want to monitor. If you want to remove a service from the Services To Monitor list, highlight it and click Remove.
- Attempt To Restart This Service After Each Failure - When this option is enabled, if a service fails the monitor check, SyncSafe Replicate will attempt to restart it.
- During this restart period, SyncSafe Replicate will not check the other services, to avoid any false failures while the one service is attempting to be restarted. If the service cannot be restarted, SyncSafe Replicate will consider this a failure.
Failover Options
Note
If you want to disable failover monitoring completely, you must disable Failover Shares, Failover Host Name, and Failback Host Name; and do not specify anything for the failover and failback scripts. Additionally, you must select Retain Target Network Configuration in the Failover Identity section. If you select any of these options or choose Apply Source Network Configuration To The Target under Failover Identity, a failover monitor will be created.
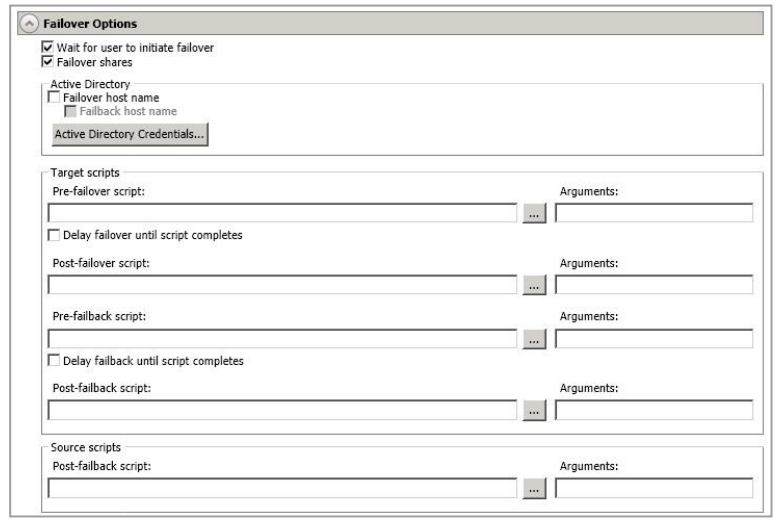
Option Details
- Wait For User To Initiate Failover - The failover process can wait for you to initiate it, allowing you to control when failover occurs. When a failure occurs, the job will wait in Failover Condition Met for you to manually initiate the failover process. Disable this option if you want failover to occur immediately when a failure occurs.
-
Failover shares—Select this option to failover shares to the target. Only the shares that you selected on the Choose Data page will be protected and failed over.
Note
Share failover only occurs for standard Windows file system shares. Other shares must be configured for failover through the failover scripts or created manually on the target. See Shares Information on the Troubleshooting Page for more information.
Note
If you are failing over Windows shares but your source and target do not have the same drive letters, you must use the All to One selection under Path Mapping when establishing your job. Otherwise, the shares will not be created on the target during failover.
Note
Windows share information is automatically updated on the target every 30 seconds.
-
Failover Host Name - If desired, you can failover the source server's host name. This will automatically remove the host SPN (Service Principal Name) from Active Directory on the source and add it to Active Directory on the target. If you are using Active Directory, enable this option or you may experience problems with failover.
- Failback Host Name - This option returns the host SPN on the source and target back to their original settings on failback. If you are using Active Directory, enable this option or you may experience problems with failback.
- Active Directory Credentials - If you are failing over and/or failing back the host name, you need to specify a user that has update privileges within Active Directory. Click Active Directory Credentials and identify a user and the associated password that has privileges to create and delete SPNs. The username must be in the format fully_qualified_domain\user, and the account password cannot be blank.
Scripts
You can customize failover and failback by running scripts on the source and target.
- Scripts may contain any valid Windows command, executable, or batch file.
- The scripts are processed using the same account running the Double-Take Management service, unless you have identified a specific account through the server's properties. See Script Credentials on the Troubleshooting Page for more information.
- Examples of functions specified in scripts include:
- Stopping services on the target before failover because they may not be necessary while the target is standing in for the source.
- Stopping services on the target that need to be restarted with the source’s machine name and/or IP address.
- Starting services or loading applications that are in an idle, standby mode waiting for failover to occur.
- Notifying the administrator before and after failover or failback occurs.
- Stopping services on the target after failback because they are no longer needed.
- Stopping services on the target that need to be restarted with the target machine’s original name and/or IP address.
- There are four types of failover and failback scripts that run on the target and one failback script that runs on the source:
- Pre-Failover Script -This script runs on the target at the beginning of the failover process. Specify the full path and name of the script file.
- Post-Failover Script - This script runs on the target at the end of the failover process. Specify the full path and name of the script file.
- Pre-Failback Script - This script runs on the target at the beginning of the failback process. Specify the full path and name of the script file.
- Delay Until Script Completes (checkbox) - Enable this option if you want to delay the failover or failback process until the associated script has completed. If you select this option, make sure your script handles errors,otherwise the failover or failback process may never complete if the process is waiting on a script that cannot complete.
- Post-Failback Script - This script runs on the target or source at the end of the failback process. Specify the full path and name of the script file.
- Script Arguments Field - For each of the script types, in this field specify a comma-separated list of valid arguments required to execute the script.
Failover Identity
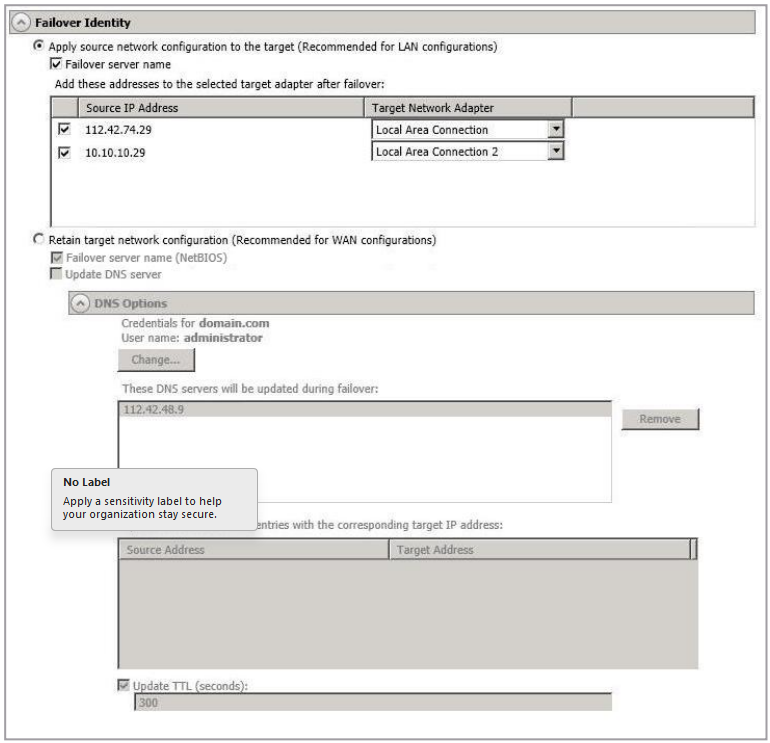
Important!
If you have selected to failover shares under the Failover Options sections, the source NetBIOS name will automatically be failed over so that the shares can be accessed after failover.
If you want to disable the ability to failover, you must select Retain Target Network Configuration. Additionally, in the Failover Options section, you must disable Failover Shares, Failover Host Name, and Failback Host Name; and do not specify anything for the failover and failback scripts. If you select any of these options or choose Apply Source Network Configuration To The Target, the ability to failover will not be disabled.
Option Details
- Apply Source Network Configuration To The Target - If you select this option, you can configure the source IP addresses to failover to the target. If your target is on the same subnet as the source (typical of a LAN environment), you should select this option. Do not select this option if you are using a NAT environment that has a different subnet on the other side of the router.
- Do not apply the source network configuration to the target in a WAN environment unless you have a VPN infrastructure so that the source and target can be on the same subnet, in which case IP address failover will work the same as a LAN configuration. If you do not have a VPN, you can automatically reconfigure the routers via a failover script (by moving the source's subnet from the source's physical network to the target's physical network). There are a number of issues to consider when designing a solution that requires router configuration to achieve IP address failover. Since the route to the source's subnet will be changed at failover, the source server must be the only system on that subnet, which in turn requires all server communications to pass through a router. Additionally, it may take several minutes or even hours for routing tables on other routers throughout the network to converge.
- Failover Server Name - Select this option to failover the server name to the target. SyncSafe Replicate checks the hosts file and uses the first name there. If there is no hosts file, SyncSafe Replicate will use the first name in DNS. (Keep in mind, the first name in DNS may not always be the same each time the DNS server is rebooted.) Lastly, if there is no DNS server, SyncSafe Replicate will use the failover monitor name created by the OpenText Replication Console. If you have selected to failover shares under the Failover Options sections, the server name will automatically be failed over so that the shares can be accessed after failover.
- Add These Addresses To The Selected Target Adapter After Failover - Select which IP addresses you want to failover and select the Target Network Adapter that will assume the IP address during failover.
- If you have inserted your source server into the console using a reserved IP address, do not select the reserved IP address for failover.
- If you configured failover to be triggered when all monitored IP addresses fail and are failing over more IP addresses than you are monitoring, you may have IP address conflicts after failover. For example, if you monitor two out of three addresses, and those two addresses fail but the third one does not, and you failover all three IP addresses, the third address that did not fail may exist on both the source and the target, depending on the cause of the failure.Therefore, when a source is failing over more IP addresses than are being monitored, there is a risk of an IP address conflict.
- Retain Target Network Configuration - If you select this option, the target will retain all of its original IP addresses. If your target is on a different subnet (typical of a WAN or NAT environment), you should select this option.
- Failover Server Name - Select this option if you want to failover the NetBIOS name.
- DNS Options:
- Update DNS Server - Specify if you want SyncSafe Replicate to update your DNS server on failover. If DNS updates are made, the DNS records will be locked during failover. Be sure and review the job requirements for updating DNS.
- Note: DNS updates are not available for Server Core servers or source servers that are in a workgroup.
- Make sure port 53 is open for DNS protocol from the target to the DNS servers so the target can discover the source DNS records.
- Expand the DNS Options section to configure how the updates will be made. The DNS information will be discovered and displayed. If your servers are in a workgroup, you must provide the DNS credentials before the DNS information can be discovered and displayed.
- Change - If necessary, click this button and specify a user that has privileges to access and modify DNS records. The account must be a member of the DnsAdmins group for the domain, and must have full control permissions on the source's A (host) and PTR (reverse lookup) records. These permissions are not included by default in the DnsAdmins group.
- Remove - If there are any DNS servers in the list that you do not want to update, highlight them and click Remove.
- Update These Source DNS Entries With The Corresponding Target IP Address - For each IP address on the source, specify what address you want DNS to use after failover.
- Update TTL - Specify the length of time, in seconds, for the time to live value for all modified DNS A records. Ideally, you should specify 300 seconds (5 minutes) or less.
DNS Notes
DNS updates will be disabled if the target server cannot communicate with both the source and target DNS servers.
If you select Retain Your Target Network Configuration but do not enable Update DNS Server, you will need to specify failover scripts that update your DNS server during failover, or you can update the DNS server manually after failover. This would also apply to non-Microsoft Active Directory integrated DNS servers. You will want to keep your target network configuration but do not update DNS. In this case, you will need to specify failover scripts that update your DNS server during failover, or you can update the DNS server manually after failover.
Mirror, Verify & Orphaned Files
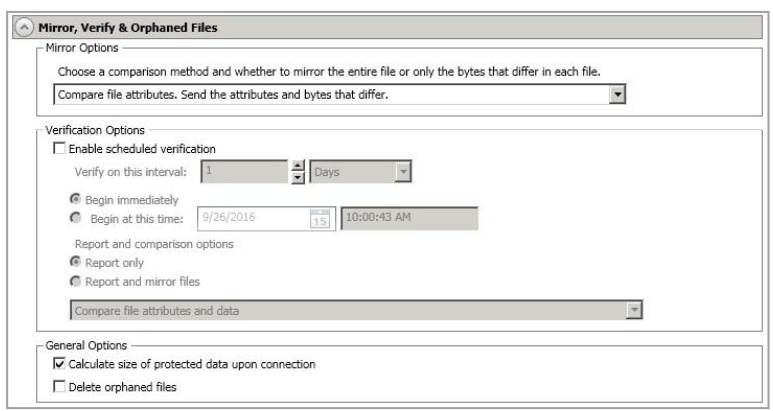
- Mirror Options - Choose a comparison method and whether to mirror the entire file or only the bytes that differ in each file.
- Do Not Compare Files. Send The Entire File. - SyncSafe Replicate will not perform any comparisons between the files on the source and target. All files will be mirrored to the target, sending the entire file. This option requires no time for comparison, but the mirror time can be slower because it sends the entire file. However, it is useful for configurations that have large data sets with millions of small files that are frequently changing and it is more efficient to send the entire file. You may also need to use this option if configuration management policies require sending the entire file.
- Compare File Attributes. Send The Entire File. - SyncSafe Replicate will compare file attributes and will mirror those files that have different attributes, sending the entire file. This option is the fastest comparison method, but the mirror time can be slower because it sends the entire file. However, it is useful for configurations that have large data sets with millions of small files that are mostly static and not changing. You may also need to use this option if configuration management policies require sending the entire file.
- Compare File Attributes. Send The Attributes And Bytes That Differ. - SyncSafe Replicate will compare file attributes and will mirror only the attributes and bytes that are different. This option is the fastest comparison method and fastest mirror speed. Files that have not changed can be easily skipped. Also files that are open and require a checksum mirror can be compared.
- Compare File Attributes And Data. Send The Attributes And Bytes That Differ. - SyncSafe Replicate will compare file attributes and the file data and will mirror only the attributes and bytes that are different. This comparison method is not as fast because every file is compared, regardless of whether the file has changed or is open. However, sending only the attributes and bytes that differ is the fastest mirror speed.
- Verification Options - Choose if you want to periodically confirm that the source replica data on the target is identical to the actual data on the source. Verification creates a log file detailing what was verified as well as which files are not synchronized. If the data is not the same, you can automatically initiate a remirror, if configured. The remirror ensures data integrity between the source and target.
- Important: Because of the way the Windows Cache Manager handles memory, machines that are doing minimal or light processing may have file operations that remain in the cache until additional operations flush them out. This may make SyncSafe Replicate files on the target appear as if they are not synchronized. When the Windows Cache Manager releases the operations in the cache on the source and target, the files will be updated on the target.
- Enable Scheduled Verification - When this option is enabled, SyncSafe Replicate will verify the source replica data on the target.
- Verify On This Interval - Specify the interval between verification processes.
- Begin Immediately - Select this option if you want to start the verification schedule immediately after the job is established.
- Begin At This Time - Select this option if you want to start the verification schedule at the specified date and time.
- Report Only - Select this option if you only want to generate a verification report. With this option, no data that is found to be different will be mirrored to the target. Choose how you want the verification to compare the files.
- Report And Mirror Files - Select this option if you want to generate a verification report and mirror data that is different to the target. Select the comparison method and type of mirroring you want to use. See the previous mirroring methods described under Mirror Options.
-
General Options - Choose your general mirroring options.
- Calculate size of protected data upon connection—Specify if you want SyncSafe Replicate to determine the mirroring percentage calculation based on the amount of data being protected. If you enable this option, the calculation will begin when mirroring begins. For the initial mirror, the percentage will display after the calculation is complete, adjusting to the amount of the mirror that has completed during the time it took to complete the calculation. Subsequent mirrors will initially use the last calculated size and display an approximate percentage. Once the calculation is complete, the percentage will automatically adjust down or up to indicate the amount that has been completed. Disabling calculation will result in the mirror status not showing the percentage complete or the number of bytes remaining to be mirrored.
Note
The calculated amount of protected data may be slightly off if your data set contains compressed or sparse files.
-
Delete Orphaned Files - An orphaned file is a file that exists in the replica data on the target, but does not exist in the protected data on the source. This option specifies if orphaned files should be deleted on the target.
- Orphaned file configuration is a per target configuration. All jobs to the same target will have the same orphaned file configuration.
- If delete orphaned files is enabled, carefully review any replication rules that use wildcard definitions. If you have specified wildcards to be excluded from protection, files matching those wildcards will also be excluded from orphaned file processing and will not be deleted from the target. However, if you have specified wildcards to be included in your protection, those files that fall outside the wildcard inclusion rule will be considered orphaned files and will be deleted from the target.
- The orphaned file feature does not delete alternate data streams. To do this, use a full mirror, which will delete the additional streams when the file is re-created.
- If you want to move orphaned files rather than delete them, you can configure this option along with the move deleted files feature to move your orphaned files to the specified deleted files directory. See Target Server Properties on the Server Properties Explained page for more information.
Network Route
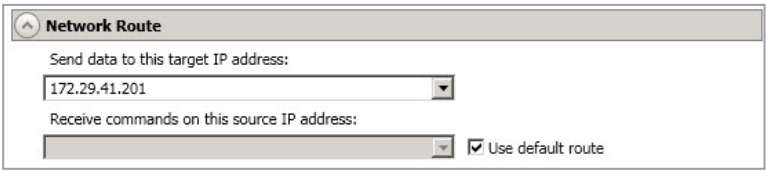
This section allows you to control the IP address to which you're sending data for the job. By default, the IP address will be the main address of the server as registered in the console. However, there may be cases for File and Folder Replication jobs where an alternate IP needs to be used.
Cluster Considerations
If your target is a cluster, you will see a table presented where you can select the target route, rather than the single target route field as shown above. The field functions the same as described below.
- Send Data To This Target IP Address - By default, SyncSafe Replicate will select an IP address on the target for transmissions. If desired, specify an alternate route on the target that the data will be transmitted through. This allows you to select a different route for SyncSafe Replicate traffic. For example, you can separate regular network traffic and SyncSafe Replicate traffic on a machine with multiple IP addresses. You can also select or manually enter a public IP address (which is the public IP address of the server's router) if you are using a NAT environment. If you enter a public IP addresses, you will see additional fields allowing you to disable the default communication ports and specify other port numbers to use, allowing the target to communicate through a router. The Management Service port is used to persist the source share configuration when shares are being protected. The Replication Service port is used for data transmission.
- If you change the IP address on the target which is used for the target route, you will be unable to edit the job. If you need to make any modifications to the job, it will have to be deleted and re-created.
- Receive Commands On This Source IP Address - By default, SyncSafe Replicate will select an IP address on the source to receive commands and requests for status from the target. This is communication from the Double-Take Management Service. If desired,specify an alternate route on the source that the commands and requests will be transmitted to. This allows you to select a different route for SyncSafe Replicate management communication. You can also manually enter a public IP address (which is the public IP address of the source server's router) if you are using a NAT environment.
- Use Default Route - Select this option to disable the drop-down list that allows you to select the route from the target server. When this option is enabled, the default route will automatically be used.
Path Mapping
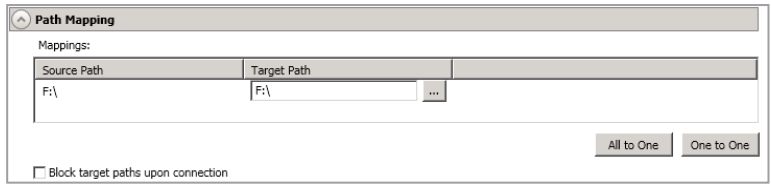
Path Mappings allow you to specify the location on the target where the replica of the source data will be stored. By default, the replica source data will be stored in the same directory structure on the target. Make sure you update this location if you are protecting multiple sources or jobs to the same target. If your target is a standalone server, you have two pre-defined locations as well as a custom option that allows you to set your path. If your target is a cluster, the target mapping will be blank and you will have to specify a custom location.
Options:
- All To One - Click this button to set the mapping so that the replica source data will be stored on a single volume on the target. The pre-defined path is \source_name\volume_name. If you are protecting multiple volumes on the source, each volume would be stored on the same volume on the target. For example, C:\data and D:\files for the source Alpha would be stored in D:\alpha\C and D:\alpha\D, respectively.
- One To One - Click this button to set the mapping so that the replica source data will be stored in the same directory structure on the target. For example, C:\data and D:\files on the source will be stored in C:\data and D:\files, respectively, on the target.
- Custom Location - If the pre-defined options do not store the data in a location that is appropriate for your network operations, you can specify your own custom location where the replica source data will be stored. Click the Target Path and edit it, selecting the appropriate location.
-
Use Defaults - Click this button to reset the Target Path location back to its blank default setting. This option is only available if your target is a cluster.
File and Folder Replication - Path Mapping Considerations
- If you are protecting system state data (like your Program Files or Documents and Settings directory), you must select the All to One mapping or specify a customized location in order to avoid sharing violations. Keep in mind that this mapping will avoid sharing violations on the target, however during a restoration, you will get sharing violations on the source because the restoration mapping is one to one and your system state files will be in use on the source you are restoring to. In this case, restoration will never complete. If you will need to restore data and you must protect system state data, you should use a full server job.
- If you are protecting dynamic volumes or mount points, your location on the target must be able to accommodate the amount of data that may be stored on the source.
- If you are protecting multiple mount points, your directory mapping must not create a cycle or loop. For example, if you have the C: volume mounted at D:\C and the D: volume mounted at C:\D, this is a circular configuration. If you establish a job for either C:\D or D:\C, there will be a circular configuration and SyncSafe Replicate mirroring will never complete.
- If you are protecting sparse files, the amount of disk space available must be equal to or greater than the entire size of the sparse file. If the target location is an NTFS 5 volume, the amount of disk space available must be equal to or greater than the on-disk size of the sparse file.
-
Block target paths upon connection—You can block writing to the replica source data located on the target. This keeps the data from being changed outside of SyncSafe Replicate processing. Any target paths that are blocked will be unblocked automatically during the failover process so that users can modify data after failover. During restoration, the paths are automatically blocked again. If you failover and failback without performing a restoration, the target paths will remain unblocked.
Failover Services
This option allows you to specify services to stop on the source and start on the target during failover, and to start on the source and stop on the target during failback. Click Add to insert a service into the list or Remove to remove a service from the list. The services will be started in the order they appear and stopped in the reverse order. Highlight a service and click Move Up or Move Down to arrange the services in the desired order.
You will also have the option at failover time to override the stopping of services. If desired, you can select Leave source services running for live and snapshot failover.
For use cases where the File and Folder Replication job is intended to maintain parity of production data for existing applications, and application services need to be disabled/enabled to facilitate cutover without creating conflicts between servers or continued modification of files after failover by an application through a service.
Snapshots
A snapshot is an image of the source replica data on the target taken at a single point in time. You can view the snapshots in VSS and recover any files or folders desired. However, you cannot failover to a snapshot.
Turn on Enable Scheduled Snapshots if you want SyncSafe Replicate to take snapshots automatically at set intervals.
Options
- Take Snapshots On This Interval - Specify the interval (in days, hours, or minutes) for taking snapshots.
- Begin Immediately - Select this option if you want to start taking snapshots immediately after the protection job is established.
- Begin at this time—Select this option if you want to start taking snapshots at a later date and time. Specify the date and time parameters to indicate when you want to start.
See the Managing Snapshots section of the Managing Jobs page for details on creating manual snapshots and deleting snapshots. As discussed on the Implementation Prep page, in order to limit the amount of space consumed by snapshots and prevent full disk issues, it is advisable to use Windows' Shadow Copy settings to set a limit on the amount of space VSS snapshots may consume.
Compression

To help reduce the amount of bandwidth needed to transmit SyncSafe Replicate data, compression allows you to compress data prior to transmitting it across the network. In a WAN environment this provides optimal use of your network resources. If compression is enabled, the data is compressed before it is transmitted from the source. When the target receives the compressed data, it decompresses it and then writes it to disk. You can set the level from Minimum to Maximum to suit your needs.
Keep in mind that the process of compressing data impacts processor usage on the source. If you notice an impact on performance while compression is enabled in your environment, either adjust to a lower level of compression, or leave compression disabled. Use the following guidelines to determine whether you should enable compression.
- If data is being queued on the source at any time, consider enabling compression.
- If the server CPU utilization is averaging over 85%, be cautious about enabling compression.
- The higher the level of compression, the higher the CPU utilization will be.
- Do not enable compression if most of the data is inherently compressed. Many image (.jpg, .gif) and media (.wmv, .mp3, .mpg) files, for example, are already compressed. Some images files, such as .bmp and .tif, are decompressed, so enabling compression would be beneficial for those types.
- Compression may improve performance even in high-bandwidth environments.
- Do not enable compression in conjunction with a WAN Accelerator. Use one or the other to compress SyncSafe Replicate data.
Note
All jobs from a single source connected to the same IP address on a target will share the same compression configuration.
Bandwidth
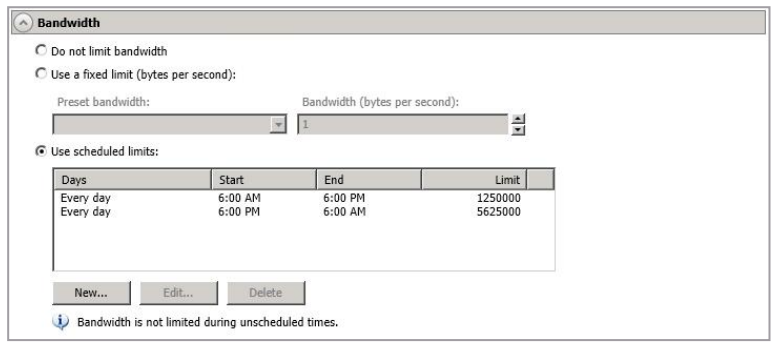
Bandwidth limitations are available to restrict the amount of network bandwidth used for SyncSafe Replicate data transmissions. When a bandwidth limit is specified, SyncSafe Replicate never exceeds that allotted amount. The bandwidth not in use by SyncSafe Replicate is available for all other network traffic.
Note
- All jobs from a single source connected to the same IP address on a target will share the same bandwidth configuration.
- The scheduled option is not available if your source is a cluster.
Options:
- Do Not Limit Bandwidth - SyncSafe Replicate will transmit data using 100% bandwidth availability.
- Use A Fixed Limit - SyncSafe Replicate will transmit data using a limited, fixed bandwidth. Select a Preset Bandwidth limit rate from the common bandwidth limit values. The Bandwidth field will automatically update to the bytes per second value for your selected bandwidth. This is the maximum amount of data that will be transmitted per second. If desired, modify the bandwidth using a bytes per second value. The minimum limit should be 3500 bytes per second.
- Use Scheduled Limits - SyncSafe Replicate will transmit data using a dynamic bandwidth based on the schedule you configure. Bandwidth will not be limited during unscheduled times.
- Click New to create a new scheduled bandwidth limit. Specify the following information.
- Daytime entry - Select this option if the start and end times of the bandwidth window occur in the same day (between 12:01 AM and midnight). The start time must occur before the end time.
- Overnight entry - Select this option if the bandwidth window begins on one day and continues past midnight into the next day. The start time must be later than the end time, for example 6 PM to 6 AM.
- Day - Enter the day on which the bandwidth limiting should occur. You can pick a specific day of the week, Weekdays to have the limiting occur Monday through Friday, Weekends to have the limiting occur Saturday and Sunday, or Every day to have the limiting repeat on all days of the week.
- Start Time - Enter the time to begin bandwidth limiting.
- End Time - Enter the time to end bandwidth limiting.
- Preset Bandwidth - Select a bandwidth limit rate from the common bandwidth limit values. The Bandwidth field will automatically update to the bytes per second value for your select bandwidth.
- Bandwidth - If desired, modify the bandwidth using a bytes per second value. The minimum limit should be 3500 bytes per second.
- Click Edit to modify an existing scheduled bandwidth limit.
- Click Delete to remove a scheduled bandwidth limit.
- Click New to create a new scheduled bandwidth limit. Specify the following information.
If you change your job option from Use Scheduled Limit to Do Not Limit Bandwidth or Use A Fixed Limit, any schedule that you created will be preserved. That schedule will be reused if you change your job option back to Use Scheduled Limits.
You can manually override a schedule after a job is established by selecting Other Job Options > Set Bandwidth. If you select No Bandwidth Limit or Fixed Bandwidth Limit, that manual override will be used until you go back to your schedule by selecting Other Job Options > Set Bandwidth > Scheduled Bandwidth Limit. For example, if your job is configured to use a daytime limit, you would be limited during the day, but not at night. But if you override that, your override setting will continue both day and night, until you go back to your schedule. See the Managing And Controlling Jobs page's section for your job type for more information on the Other Job Options.
Scripts
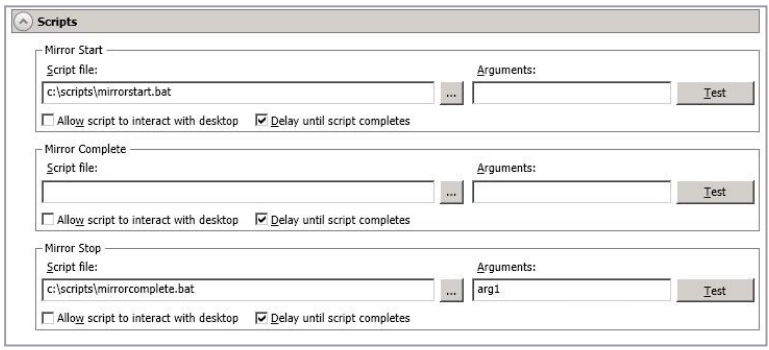
Similar to the script options available under the Failover Options settings, Mirroring scripts defined in this section may contain any valid Windows command, executable, or batch file. The scripts are processed using the same account running the Double-Take service, unless you have identified a specific account through the server's properties.
There are three types of Mirroring Scripts:
- Mirror Start - This script starts when the target receives the first mirror operation. In the case of a difference mirror, this may be a long time after the mirror is started because the script does not start until the first different data is received on the target. If the data is synchronized and a difference mirror finds nothing to mirror, the script will not be executed. Specify the full path and name of the Script file.
- Mirror Complete - This script starts when a mirror is completed. Because the mirror statistics may indicate a mirror is at 99-100% when it is actually still processing (for example, if files were added after the job size was calculated, if there are alternate data streams, and so on), the script will not start until all of the mirror data has been completely processed on the target. Specify the full path and name of the Script file.
- Mirror Stop - This script starts when a mirror is stopped, which may be caused by an auto-disconnect occurring while a mirror is running, the service is shutdown while a mirror is running, or if you stop a mirror manually. Specify the full path and name of the Script file.
The Arguments fields should contain a comma-separated list of valid arguments required to execute the script the field is associated with. The Delay Until Script Completes option should be enabled if you want to delay the mirroring process until the associated script has completed. This option should be used with care as scripts that do not include error handling may cause mirroring to hang and never complete due to an unhandled script error.
To validate your selected scripts and arguments, after configuring the fields, click Test, which will perform an execution of the scripts to confirm function. If your scripts make any changes to the target machine, you will need to manually revert those changes.
Note
If you establish mirroring scripts for one job and then establish additional jobs to the same target using the same target path mapping, the mirroring scripts will automatically be applied to those subsequent jobs. If you select a different target path mapping, the mirroring scripts will have to be reconfigured for the new job(s).
Full Server Job Specific Options
Full Server Protection Job options are largely the same as those for File and Folder Protection jobs. This section will cover the options that are unique to full server protection jobs.
Test Failover
If you have built an additional Virtual Machine to be used as a Test Failover target, you will configure it in this section. Keep in mind the following for using the test failover feature:
- The network adapters on the test failover machine must have the same friendly name as the network adapters you have mapped for live failover in the Network Adapter Options section. For example, if you have Local Area Network mapped to Local Area Network, the test failover machine must have an adapter named Local Area Network. If you have Local Area Network mapped to Network 2, and the test failover machine does not have an adapter named Network 2, test failover will fail.
- The source, target, and protection job will remain online and uninterrupted during the test.
- During the test, any scheduled snapshots for the protection job will be deferred until after the test server is online.
- The test will be performed using the test failover settings configured during job creation.
- The test failover will take a snapshot of the current data on the target and mirror the data from the snapshot to the test failover machine using the same mirroring options as the protection job.
- Once the mirror is complete, the test failover machine is rebooted automatically to finalize the test failover process.
- The test failover machine will maintain its own identity during the test.
- The test failover machine will maintain its own networking which keeps it isolated from the rest of the network in order to avoid network conflicts and redirecting clients. Applications or functionality that relies on the source networking may not be fully testable with the test machine networking.
- When using the test failover machine, log in with local credentials to avoid trust relationship issues.
- When you are finished with your test, undo it.
- When you undo a test failover, the snapshot will be maintained or deleted as specified in the test failover settings of the protection job.
- At any time during a test failover, you can undo the test, perform a live failover, or failover to a snapshot, including your test failover snapshot. (Performing a live failover or failing over to a snapshot will automatically undo any test in progress.)
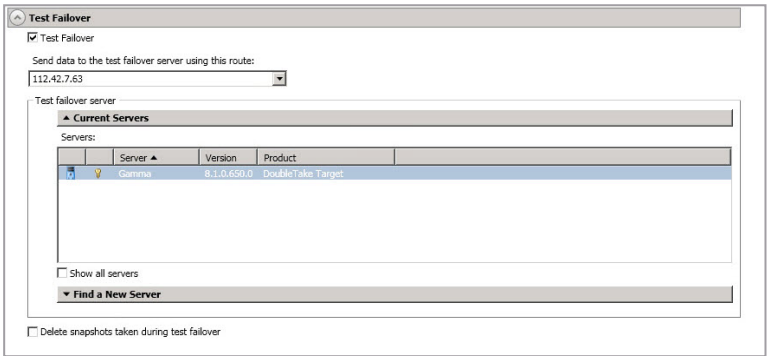
Option Details
- Test Failover - Enable this option to be able to perform test failover. Note that this option is not selectable if you do not have sufficient target VMs available in your console.
- Send Data To The Test Failover Server Using This Route - Select or enter a route to use on the test failover server for mirroring the data from the snapshot to the test failover server.
- Test Failover Server - Select the server you want to use for the test failover.
- Current Servers - This list contains the servers currently available in your console session. Servers that are not applicable to test failover will be filtered out of the list. Select your test failover server from the list. If the server you are looking for is not displayed, enable
Show All Servers. The servers in red are not available. Hover your mouse over an unavailable server to see a reason why this server is unavailable. - Find a New Server—If the server you need is not in the
Current Serverslist, click theFind a New Serverheading. From here, you can specify a server along with credentials for logging in to the server. If necessary, you can clickBrowseto select a server from a network drill-down list. After you have identified or located the server, clickAdd Server. If there are any issues connecting to that server, you will see an error in yellow at the top of the page. If there are no issues, you can continue.
- Current Servers - This list contains the servers currently available in your console session. Servers that are not applicable to test failover will be filtered out of the list. Select your test failover server from the list. If the server you are looking for is not displayed, enable
- Delete snapshots taken during test failover—Select this option if you want to delete the snapshots taken for the test failover process. If you disable this option, the snapshots will not be deleted when you perform undo failover.
Reverse Protection and Routing
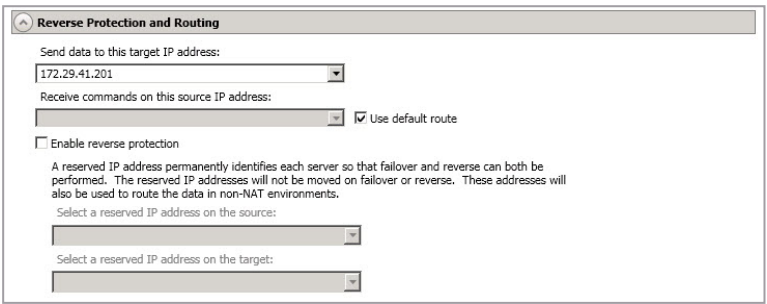
- Send Data To This Target IP Address - By default, SyncSafe Replicate will select an IP address on the target for transmissions. If desired, specify an alternate route on the target that the data will be transmitted through. This allows you to select a different route for SyncSafe Replicate traffic. For example, you can separate regular network traffic and SyncSafe Replicate traffic on a machine with multiple IP addresses. You can also select or manually enter a public IP address (which is the public IP address of the server's router) if you are using a NAT environment. If you enter a public IP addresses, you will see additional fields allowing you to disable the default communication ports and specify other port numbers to use, allowing the target to communicate through a router. The Management Service Port is used to persist the source share configuration when shares are being protected and for communication after a reverse. The Replication Service Port is used for data transmission.
- Receive Commands On This Source IP Address - By default, SyncSafe Replicate will select an IP address on the source to receive commands and requests for status from the target. This is communication from the Double-Take Management Service. If desired, specify an alternate route on the source that the commands and requests will be transmitted to. This allows you to select a different route for SyncSafe Replicate management communication. You can also manually enter a public IP address (which is the public IP address of the source server's router) if you are using a NAT environment.
- Use Default Route - Select this option to disable the drop-down list that allows you to select the route from the target server. When this option is enabled, the default route will automatically be used.
Enabling Reverse Protection
By checking the Enable Reverse Protection checkbox, reverse replication will be enabled. Without reverse replication after failover, your target server is lost. If enabled, reverse protection allows you to store a copy of the target's system state on the source server, so that the target server will not be lost. The reverse process will bring the target identity back on the source hardware and establish protection. After the reverse, the source (running on the original target hardware) will be protected to the target (running on the original source hardware).
If you do not use reverse protection, after a failover, your target server will be lost. In order to continue protecting your data, you will have to manually rebuild your original source and restart protection, which can be a long and complicated process. Also, if you disable reverse, you will lose the activated target license after failover.
You may want to consider having two IP addresses on each server. This will allow you to monitor and failover one (or more) IP addresses, while still leaving an IP address that does not get failed over. This IP address that is not failed over is called a reserved IP address and can be used for the reverse process. The reserved IP address remains with the server hardware. Ideally, the reserved IP address should not be used for production communications. The reserved IP address can be on the same on different subnet from your production IP addresses, however if the subnet is different, it should be on a different network adapter. The reserved IP addresses will also be used to route SyncSafe Replicate data.
You do not have to have a second IP address on each server. It is acceptable to use the production IP address for reverse protection, as long as you are selecting the option to retain the target configuration.
Reverse Replication Reserved IP Field Options
- Select A Reserved IP Address On The Source - Specify an IP address on the source which will be used to permanently identify the source server. The IP address you specify will not be failed over to the target in the event of a failure. This allows you to reverse protection back to the source after a failover.
- Send Data To Source After Reverse Using This Route - This field will only be displayed if the console recognizes that your source address is a public NAT address. In that case, you can specify the route and disable the default communication port and specify another port number to use for data transmission.
- Select A Reserved IP Address On The Target - Specify an IP address on the target which will be used to permanently identify the target server. The IP address you specify will not be lost during failover. This allows you to reverse protection back to the source after a failover. In a non-NAT environment, this address will override the target route above and be used to route the data to the target server.
Reverse Protection Considerations
When reverse protection is enabled, your source server must have space to store, process, and apply the target's system state data. See Full Server Protection Requirements for estimates on the amount of space you may need.
When the job is first started and reverse protection is enabled, an image of the target's system state is mirrored to the source server. This mirror may cause a performance impact on your source server. This impact is only temporary, and system performance will return to normal when the reverse protection mirror is complete.
To maintain system performance on the source, the target's system state is not continuously replicated to the source. You can manually update the image of the target's system state by viewing the job details and clicking Update under Target Server Image.
Network Adapter Options
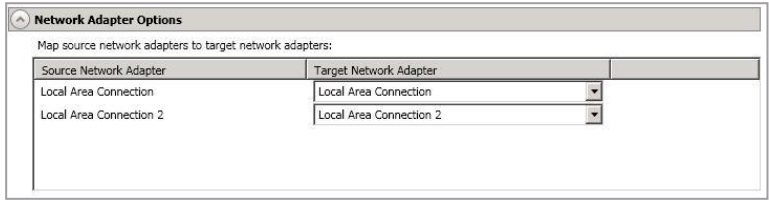
For Map Source Network Adapters To Target Network Adapters, specify how you want the IP addresses associated with each NIC on the source to be mapped to a NIC on the target. Do not mix public and private networks. Also, if you have enabled reverse protection, make sure that your NICs with your reserved IP addresses are mapped to each other.
Staging Folder Options
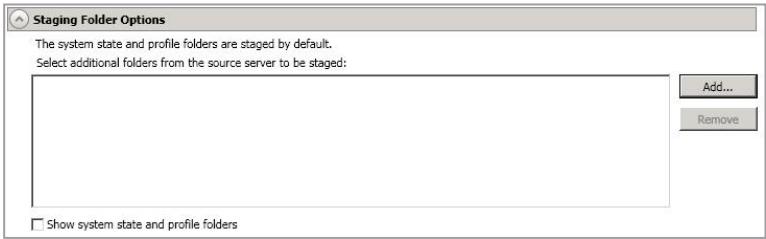
- Select additional folders from the source that need to be staged—Applications running on the target that cannot be stopped will cause retry operations because SyncSafe Replicate will be unable to write to open application files. In this case, you will want to mirror those application files to a staging location instead of their actual location. Generally, this will only apply to applications that are not installed in the Windows Program Files directory. In this case, click Add and specify the folder that you want staged. Any staged folders will be applied to their actual installation location during failover.
- Show system state and profile folders—This option displays the list of essential system state and profile folders that will be staged automatically. These essential items are displayed in a lighter color than folders you have manually added, and they cannot be removed from the list.
IIS Notes
If IIS is being used as a software application on your source but as a hardware platform manager by your hardware vendor on your target, you need to add the INetPub directory to the Staged Folders Options list. If IIS is being used as a hardware platform manager by your hardware vendor on both the source and target, you need to go to the Choose Data page and remove the INetPub directory from replication under the Replication Rules heading.
Target Services
- Services To Leave Running On The Target Server During Protection - SyncSafe Replicate controls which services are running and stopped on the target during protection. You can specify which services you want to keep running by clicking Add and selecting a service from the list. If you want to remove a service from the list, highlight it and click Remove. By default, services are stopped on the target to protect against retry operations. Do not leave services running unless absolutely necessary.
- Show Essential Services - This option displays the list of essential services that will remain running on the target. The essential services are displayed in a lighter color than services you have manually added. The essential services cannot be removed from the list.